Security operations centre

A dedicated service to defend against cyber-attacks, protect sensitive data, and ensure informational assets maintain their confidentiality, integrity and availability.
This service is currently in beta and therefore some of the specifics on this page may change. We will be launching the security operations centre for general availability in early 2025.
About the service
We are developing the security operations centre (SOC) to meet the sector's need for robust cyber security measures in today’s rapidly evolving digital landscape.
A managed security operations centre is a centralised facility where a team of cybersecurity experts work together to monitor, detect, analyse, and respond to various security incidents within an organisation’s digital infrastructure. The primary objective of a SOC is to minimise the impact of cyber-attacks, protect sensitive data, and ensure the confidentiality, integrity, and availability of your organisation’s information assets.
Download our SOC brochure (pdf) to learn more about the benefits of our security operations centre.
“This is more than just a service; it’s a commitment to a safer digital future. By providing advanced threat detection and response capabilities, we’re empowering our community to innovate with confidence.”
David Batho, director of security, Jisc
Why choose a managed SOC
With cyber-attacks becoming increasingly sophisticated and frequent, a managed SOC adds that essential extra layer of protection for organisations of all sizes through:
- Proactive threat detection: Continuously monitoring networks, systems, and applications to identify potential vulnerabilities and detect any signs of malicious activity.
- Industry-leading technology: Our leading partnerships help us react quickly and seamlessly. Our SOC will collect and analyse data from across your entire IT environment, providing a comprehensive security solution.
- Rapid incident response: As the trusted ISP for the UK’s education and research community, our visibility across the Janet Network means that when a security incident is detected, the SOC team quickly takes action to contain the threat and minimise damage, ultimately reducing the overall impact on your organisation.
- Compliance assurance: By implementing security best practices and industry-standard frameworks, SOCs help your organisation adhere to regulatory requirements and maintain compliance with data protection laws.
- Improved security posture: The combination of advanced technology, skilled personnel, and well-defined processes in a SOC helps your business maintain a strong security posture in the face of evolving threats.
- Trusted partnership: We are your trusted and vital sector partner. Our SOC offers collaborative defence to share intelligence and enhance security across the education and research sector. We will provide you with enhanced control over your security systems, helping you stay one step ahead of cyber threats.
Alt text for SOC graphic
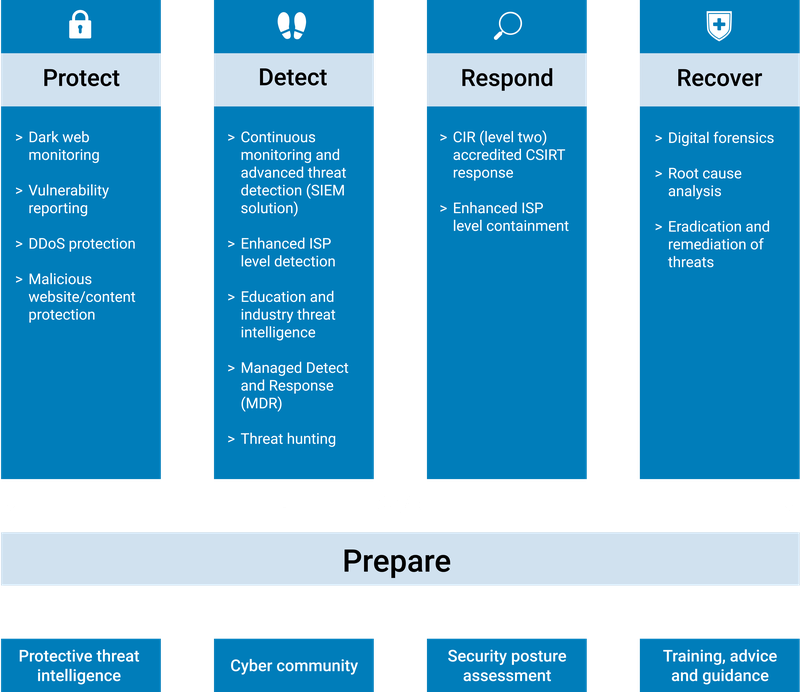
Protect
- Dark web monitoring
- Vulnerability reporting
- DDoS protection
- Malicious website/content protection
Detect
- Continuous monitoring and advanced threat protection (SIEM solution)
- Enhanced ISP level detection
- Education and industry threat intelligence
- Managed Detect and Response (MDR)
- Threat hunting
Respond
- CIR (level two) accredited CSIRT response
- Enhanced ISP level containment
Recover
- Digital forensics
- Root cause analysis
- Eradication and remediation of threats
Prepare
- Proactive threat intelligence
- Cyber community
- Secure posture assessment
- Training, advice and guidance
Protect
- Dark web monitoring
- Vulnerability reporting
- DDoS protection
- Malicious website/content protection
Detect
- Continuous monitoring and advanced threat protection (SIEM solution)
- Enhanced ISP level detection
- Education and industry threat intelligence
- Managed Detect and Response (MDR)
- Threat hunting
Respond
- CIR (level two) accredited CSIRT response
- Enhanced ISP level containment
Recover
- Digital forensics
- Root cause analysis
- Eradication and remediation of threats
Prepare
- Proactive threat intelligence
- Cyber community
- Secure posture assessment
- Training, advice and guidance
Data access
You do not have to grant Jisc access to all of your your data. Any SOC needs access to your security controls, relevant log files and similar. We do not require (and nor should any SOC provider) access to your sensitive datasets.
Prerequisites
You must have a supported EDR/MDR deployed. Currently, our SOC supports Microsoft Defender and CrowdStrike.
How to prepare for the SOC
Subscribe to the cyber security threat monitoring service which will be a core part of the security operations centre and a key stepping stone to the new service.
Completing a cyber security assessment can also help to prepare your organisation for the security operations centre and help ensure you get the most value from it. It is also important to ensure that you are first using all the core services included with your Janet connection.
Containment options during a cyber incident
The approach is broadly broken down into the following areas:
- Full containment - blocking all inbound connections with no exceptions
- Partial containment - blocking all inbound connections with exclusions such as Microsoft services (M365, etc), IP telephony services, EDR communication (CrowdStrike, Sophos, Defender XDR, etc). Partial containment works well as it allows certain business, security, and recovery solutions to continue working and hugely speeds up the recovery process. We also have the flexibility to contain individual systems like remote access solutions during less major incidents.
- Scheduled containment - can combine the above, but on a scheduled basis ie full or partial containment 6pm to 8am only (good for providing staff respite during out of office hours).

Jisc is an approved supplier on the Crown Commercial Services G-Cloud framework and Cyber Security 3 dynamic purchasing system (DPS).
Visit the Crown Commercial Services website for more information and guidance on how to purchase G-Cloud 14 and Cyber Security Services 3.
ISO certification
This service is included within the scope of our ISO9001 and ISO27001 certificates. Read more about International Organisation for Standardisation (ISO) standards and view Jisc certificates.

